

Video Training → Art-Wod - Online drawing courses + Classroom Sessions by Antonio Stappaerts
Published by: LeeAndro on 10-10-2021, 22:29 |  0
0

File Size :2.2 GB
The Drawing program, which are online drawing courses, offers bi-weekly assignments that cover all fundamental skills of drawing. You will have access to both Recreational and Hardcore assignments. Learning to draw is a crucial skill to master before becoming an efficient painter. This program will exponentially boost your confidence when drawing from both reference and imagination!
Video Training → Alexander Talyuk - Natural Retouching Portrait
Published by: LeeAndro on 10-10-2021, 22:29 |  0
0

File Size :1.7 GB
This is a class about naturalness and naturalness in photography. This is the trend of recent years: no one is already correcting a persons features - on the contrary, a bright personality is emphasized, we only embellish it a little. How to catch this trend How to fit into the new reality, if at the retouching courses you were taught, mainly, correcting flaws What is considered a drawback, and what is a feature This is a very complex and interesting question that Alexander Talyuk will brilliantly answer with his new class.
Video Training → Python Interactive Algorithmic Trading Assistant with APIs
Published by: LeeAndro on 10-10-2021, 19:59 |  0
0

MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Genre: eLearning | Language: English + srt | Duration: 58 lectures (6h 20m) | Size: 3.4 GB
Basic Python skills (variable assignments and type recognition, functions and importing libraries) are recommended.
Video Training → Certified Psychic Self Defense & Evil Entity Removal Healer
Published by: LeeAndro on 10-10-2021, 19:59 |  0
0

MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Genre: eLearning | Language: English + srt | Duration: 110 lectures (5h 53m) | Size: 6 GB
Energy cord cuttings.
Video Training → Data Analysis In-Depth (With Python)
Published by: LeeAndro on 10-10-2021, 19:39 |  0
0

MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Genre: eLearning | Language: English + srt | Duration: 23 lectures (52h 39m) | Size: 17.9 GB
No Pre-requisite required.
Video Training → Gumroad - Normal Edge Decal Tutorial HQ PDF + Unity Shader by Leonardo Iezzi
Published by: Minhchick on 10-10-2021, 18:53 |  0
0
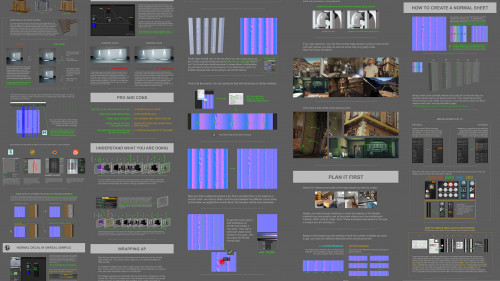
Gumroad - Normal Edge Decal Tutorial HQ PDF + Unity Shader by Leonardo Iezzi
English | Size: 15.8MB
Category: Tutorial
wanted to share this tutorial I made in my own free time regarding the Normal Edge decals.
Video Training → Gumroad Alien Outlaws 2D Design and Brainstorming
Published by: Minhchick on 10-10-2021, 18:50 |  0
0

Gumroad Alien Outlaws 2D Design and Brainstorming TUTORiAL-SOFTiMAGE
English | Size: 265.65 MB
Category: Tutorial
In this tutorial I focus on designing 20 Alien Outlaw characters from the initial rough in, to clean line, and then flat color.
Video Training → SDR for Ethical Hackers and Security Researchers 3.0 | Udemy
Published by: Minhchick on 10-10-2021, 18:47 |  0
0

SDR for Ethical Hackers and Security Researchers 3.0 | Udemy
English | Size: 1.13GB
Category: Tutorial
Learn how to use the Complete Power of HackRF One Board to find Different Vulnerabilities in Different Wireless Devices
Video Training → AlgoZenith - Applied Algo & DS for Coding Competitions [AZ-202]
Published by: Minhchick on 10-10-2021, 18:43 |  0
0
![AlgoZenith - Applied Algo & DS for Coding Competitions [AZ-202] AlgoZenith - Applied Algo & DS for Coding Competitions [AZ-202]](https://i115.fastpic.org/big/2021/1009/45/f492d9ce2fe3633795445df8ff4ef645.png)
AlgoZenith - Applied Algo & DS for Coding Competitions [AZ-202]
English | Size: 9.58 GB
Category: CBTs
Strengthening the Important topics needed in Competitive Programming and Learning various New applications of them
Video Training → Microsoft - Cybersecurity Pro Track Managing Identity
Published by: Minhchick on 10-10-2021, 18:37 |  0
0

Microsoft - Cybersecurity Pro Track Managing Identity
English | Size: 809.32 MB
Category: Tutorial
In this course, we will examine the concepts of understanding the importance of securing identity and privileged access through combinations of encryption,



