

Video Training → Ask Video Audio Roli Equator 101 Equator 2 Explored TUTORiAL
Published by: voska89 on 3-06-2022, 07:58 |  0
0

Ask Video Audio Roli Equator 101 Equator 2 Explored TUTORiAL
Home Page
https://bit.ly/3PK8klA
Genre / Category:Sound & Production
File Size :562MB
Product Details Equator2 is a revolutionary hybrid MPE synthesizer from ROLI. Watch this course by expert trainer Rishabh Rajan, and learn to create any sound imaginable using this expressive super synth.
Portable → Movavi Video Suite 22.3.0 Multilingual + Portable
Published by: voska89 on 2-06-2022, 14:34 |  0
0

Movavi Video Suite 22.3.0 (x86/x64) Multilingual + Portable | 143.9/151/285.3 Mb
Movavi Video Suite is comprehensive video making software that helps you create professional-looking movies and slideshows on your home computer - even if you have no experience.Incorporate music, create text captions, apply visual effects and transitions - you can do whatever you want with your video. In addition to the video making app, Movavi Video Suite contains a number of useful apps to help every video maker: powerful video converter that supports 180+ media formats, convenient utility for burning DVDs, a special tool for digitizing analog video, and more. Making video with Movavi is easy and fun! So, let's get started!
Portable → Aiseesoft Video Converter Ultimate 10.5.12 (x64) Portable Multilingual
Published by: voska89 on 2-06-2022, 14:31 |  0
0
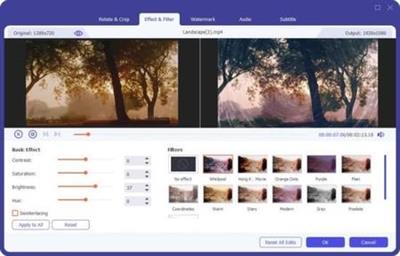
Aiseesoft Video Converter Ultimate 10.5.12 (x64) Portable Multilingual | 116 Mb
Aiseesoft Video Converter Ultimate is the powerful conversion software to assist you converting homemade DVD and videos to 2D/3D/HD video files with great video editing features and supports iPhone/iPad/iPod and most popular portable devices.
Video Training → Windows Network Security Fundamentals [Video]
Published by: voska89 on 2-06-2022, 13:16 |  0
0
![Windows Network Security Fundamentals [Video] Windows Network Security Fundamentals [Video]](https://i120.fastpic.org/big/2022/0602/71/ad1c33f985e72920c7bbf47c7d323071.jpeg)
Instructors: Glenn E. Weadock | March 2022 | Duration: 2h 24m
Video: MP4 1280x720 48 KHz | English | Size: 660 MB
Many organizations now use a hybrid environment in which existing on-premises networks are supplemented by cloud resources. The challenge is that security in such a world is even more complex than before.
Video Training → Introduction to Docker Compose [Video]
Published by: voska89 on 2-06-2022, 12:56 |  0
0
![Introduction to Docker Compose [Video] Introduction to Docker Compose [Video]](https://i120.fastpic.org/big/2022/0602/67/a59331144af0eaef10fc6534c3ed3167.jpeg)
Instructors: Sean P. Kane | March 2022 | Duration: 2h 37m
Video: MP4 1920x1080 48 KHz | English | Size: 2 GB
Containers are often advertised as solving a multitude of problems relating to delivering and maintaining highly available software in the always-on, global environment that most organizations must serve today, but how can they actually help you? What problems are you actually experiencing that can be solved with containers and its closely related technologies?
Video Training → Introduction to Docker CI/CD [Video]
Published by: voska89 on 2-06-2022, 12:56 |  0
0
![Introduction to Docker CI/CD [Video] Introduction to Docker CI/CD [Video]](https://i120.fastpic.org/big/2022/0602/f9/9d669d45bf3edb8084e61984eb0e81f9.jpeg)
Instructors: Sean P. Kane | March 2022 | Duration: 2h 33m
Video: MP4 1920x1080 44 KHz | English | Size: 1.66 GB
Video Training → Hands-On Threat Modeling [Video]
Published by: voska89 on 2-06-2022, 12:54 |  0
0
![Hands-On Threat Modeling [Video] Hands-On Threat Modeling [Video]](https://i120.fastpic.org/big/2022/0602/2b/360fb8a70ea85b51d2cc990b5b1bf22b.jpeg)
Instructors: Sebastien Deleersnyder | March 2022 | Duration: 1h 34m
Video: MP4 1920x1080 48 KHz | English | Size: 392 MB
Threat modeling (also known as architecture risk analysis) is the primary security analysis task performed during the software design stage. It is a structured activity for identifying and evaluating application threats and related design flaws. You use the identified flaws to adapt your design, or scope your security testing.
Video Training → Getting Started with Cybersecurity Science [Video]
Published by: voska89 on 2-06-2022, 12:52 |  0
0
![Getting Started with Cybersecurity Science [Video] Getting Started with Cybersecurity Science [Video]](https://i120.fastpic.org/big/2022/0602/a2/81f792d13b91479bf15342c7fa650ca2.jpeg)
Instructors: Josiah Dykstra | March 2022 | Duration: 1h 44m
Video: MP4 1920x1080 48 KHz | English | Size: 544 MB
Join Josiah Dykstra for an introduction to the application of scientific methodology to the process of creating cybersecurity tools and systems.
Video Training → Defensive Cybersecurity Fundamentals [Video]
Published by: voska89 on 2-06-2022, 12:44 |  0
0
![Defensive Cybersecurity Fundamentals [Video] Defensive Cybersecurity Fundamentals [Video]](https://i120.fastpic.org/big/2022/0602/c7/48d6ac0821e49408c2d02fcfa0855bc7.jpeg)
Instructors: Amanda Berlin | March 2022 | Duration: 2h 32m
Video: MP4 1280x720 48 KHz | English | Size: 943 MB
Everyone talks about the intrusion kill chain (sometimes called the "cyber kill chain")—a model for actionable intelligence in which defenders align enterprise defensive capabilities to the specific processes an adversary might undertake to target that enterprise. However, much of what's discussed publicly is misinformation and scare tactics.
Video Training → Architectural Katas Spring 2022 [Video]
Published by: voska89 on 2-06-2022, 12:34 |  0
0
![Architectural Katas Spring 2022 [Video] Architectural Katas Spring 2022 [Video]](https://i120.fastpic.org/big/2022/0602/dc/8db04c8c53f2eace96eaceedaae486dc.jpeg)
Instructors: Neal Ford | July 2022 | Duration: 1h 14m
Video: MP4 1920x1080 44 KHz | English | Size: 1 GB
About Architectural Katas: What could be better than practicing software architecture with your handpicked dream team of architects? Participants in Architectural Katas, moderated by Neal Ford, work together in small groups of their choosing to solve a challenge an actual organization is facing. Everyone gets the chance to practice their craft with a real software architecture problem in a safe and social environment, and the finalists and winners earn well-deserved bragging rights (not to mention an intriguing line on their résumé). Plus a selected organization will have some of its gnarliest software architecture problems solved.



