

Video Training → Linkedin - Certified Information Security Manager (CISM) Cert Prep (2022) 4 Incident Management
Published by: voska89 on 11-11-2022, 11:21 |  0
0

Released 09/2022
MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Skill Level: Advanced | Genre: eLearning | Language: English + srt | Duration: 2h 20m | Size: 500.8 MB
Even the best security controls aren't foolproof. That's why security professionals need a solid incident management plan. The fourth domain of the Certified Information Security Manager (CISM) exam—Information Security Incident Management—tests your mastery of this important topic. Take this CISM Cert Prep course to study for the exam and gain a deeper understanding of how your team should react to and resolve a security incident, whether it's an attack on your network, an email-born virus, or data theft. Instructor Mike Chapple explains how to identify, triage, and respond to an event, minimizing the damage and maximizing your ability to find the root cause, so you can resume normal operations. He also provides tips for logging and monitoring ongoing security-related events. Each topic maps to a relevant objective from the CISM certification exam.
Video Training → Kubernetes Security Minimizing Microservice Vulnerabilities
Published by: voska89 on 11-11-2022, 10:13 |  0
0

Duration: 1h 37m | Video: .MP4, 1280x720 30 fps | Audio: AAC, 48 kHz, 2ch | Size: 165 MB
Genre: eLearning | Language: English
Microservices are secured via both code and infrastructure. This course will teach you how to secure microservices hosted within a Kubernetes environment.
What you'll learn
Video Training → Kubernetes Security Implementing Supply Chain Security
Published by: voska89 on 11-11-2022, 10:13 |  0
0

Duration: 49m | Video: .MP4, 1280x720 30 fps | Audio: AAC, 48 kHz, 2ch | Size: 92 MB
Genre: eLearning | Language: English
Kubernetes is an open-source system for automating deployment, scaling, and management of containerized applications. This course will teach you the concepts for securing the Kubernetes supply chain.
What you'll learn
Video Training → Kubernetes Security Cluster Hardening
Published by: voska89 on 11-11-2022, 10:12 |  0
0

Duration: 1h 3m | Video: .MP4, 1280x720 30 fps | Audio: AAC, 48 kHz, 2ch | Size: 126 MB
Genre: eLearning | Language: English
This course will teach you how to secure your Kubernetes clusters for production workloads.
What you'll learn
Video Training → Huawei HCIP-Security 3.0
Published by: Minhchick on 1-11-2022, 17:39 |  0
0

Huawei HCIP-Security 3.0
English | Tutorial | Size: 9.07 GB
This course is for HCIP-Security V3.0, and the course will gradually explain the following points:
Video Training → Kaspersky Security Center. Scaling (302.11) Official Materials
Published by: Minhchick on 31-10-2022, 03:41 |  0
0

Kaspersky Security Center. Scaling (302.11) Official Materials
English | Tutorial | Size: 54.4 MB
Video Training → Linkedin Learning - GitHub Advanced Security
Published by: Minhchick on 26-10-2022, 17:57 |  0
0
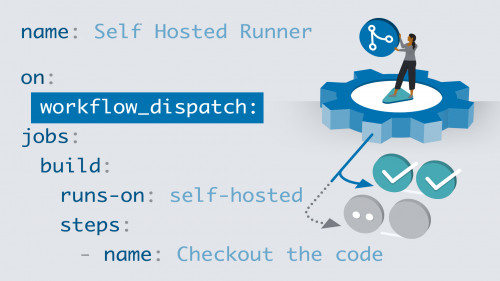
Linkedin Learning - GitHub Advanced Security
English | Tutorial | Size: 181.26 MB
GitHub is one of the most popular platforms to collaborate in the open source community.
Video Training → KodeKloud - Certified Kubernetes Security Specialist (CKS)
Published by: Minhchick on 24-10-2022, 18:08 |  0
0

KodeKloud - Certified Kubernetes Security Specialist (CKS)
English | Tutorial | Size: 1.42 GB
Kubernetes is one of the highest trending technology in Cloud Computing as of today.
Video Training → Stone River - Google Cloud Security Fundamentals
Published by: Minhchick on 16-10-2022, 18:31 |  0
0

Stone River - Google Cloud Security Fundamentals
English | Tutorial | Size: 2.49 GB
Security in the cloud is much like security in your on-premise data centers, only without the costs of maintaining facilities and hardware.
Video Training → Linkedin Learning - Cloud Security Architecture for the Enterprise
Published by: Minhchick on 16-10-2022, 05:13 |  0
0

Linkedin Learning - Cloud Security Architecture for the Enterprise-XQZT
English | Tutorial | Size: 114.60 MB
Explore the core pillars of designing a cloud security architecture, in a cloud-agnostic way that covers what a cloud security architecture should include and why



