

Video Training → Tutsplus - Secure Your WordPress Site With SSL
Published by: voska89 on 1-09-2021, 20:47 |  0
0

MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz
Language: English | Size: 82.9 MB | Duration: 9 minutes
The need today for a secure internet is greater than ever. Things like identity theft, stolen passwords, or ransomware can be avoided by implementing proper security measures. An important security best practice for the server is implementing SSL (Secure Sockets Layer) certificates, which encrypt the data between the client and the server. This secures communication between the two, ensuring that user data such as credit card numbers or passwords cannot be stolen in a man-in-the-middle attack.
Portable → Secure Eraser Professional 5.302 Multilingual Portable
Published by: voska89 on 18-08-2021, 09:20 |  0
0
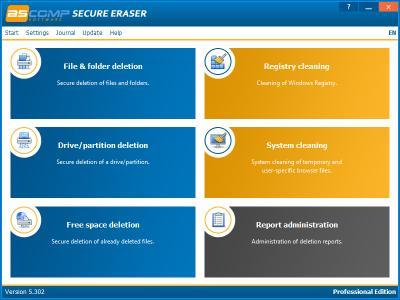
Secure Eraser Professional 5.302 Multilingual Portable | 5.5 Mb
Erase Your Documents and Drives Securely. Because it's been deleted from your hard drive, doesn't mean it's gone forever. As long as the information was not overwritten, anyone can restore it at any time. It gets even more complicated, if a computer has been resold or given away.
Video Training → Udemy - Secure - Network & Communication
Published by: voska89 on 28-07-2021, 04:36 |  0
0

MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Genre: eLearning | Language: English + srt | Duration: 14 lectures (2h 22m) | Size: 228.2 MB
Secure Networking Models, Secure Network Design, Secure Network Components, Secure Communications
Video Training → O'Reilly - Secure Programming with C
Published by: voska89 on 2-07-2021, 11:34 |  0
0

Duration: 4h 46m | Author: Howard Poston | Video: 1920x1080, 48kHz | 1.1 GB
Genre: eLearning | Language: English
Secure coding with C is a top concern. Although the C programming language, which is commonly used in numerous applications and operating systems is popular, flexible, and versatile, it is inherently vulnerable to exploitation.
Video Training → Microsoft Azure DevOps Engineer Implement a Secure and Compliant Development Process
Published by: Minhchick on 16-06-2021, 20:04 |  0
0
Microsoft Azure DevOps Engineer Implement a Secure and Compliant Development Process
English | Size: 335.72 MB
Category: Tutorial
It's no longer acceptable to just perform security testing at the end of long development cycles.
Video Training → Cloud Academy - DevSecOps - Build and Release Secure Software Faster
Published by: Minhchick on 11-06-2021, 03:50 |  0
0

Cloud Academy - DevSecOps - Build and Release Secure Software Faster
English | Size: 6.19 GB
Category: Security
In todays climate of data breaches and hacks - security has never been more paramount,
Video Training → Linkedin Learning - CSSLP Cert Prep 2 Secure Software Requirements UPDATE 2021/02/26
Published by: Minhchick on 30-05-2021, 19:56 |  0
0
Linkedin Learning - CSSLP Cert Prep 2 Secure Software Requirements UPDATE 20210226-XQZT
English | Size: 166.13 MB
Category: Tutorial
Learn how to define and validate security requirements for applications as you prepare for the second domain of the CSSLP exam: Secure Software Requirements
Video Training → Linkedin Learning - PHP Creating Secure Websites
Published by: Minhchick on 26-05-2021, 18:59 |  0
0
Linkedin Learning - PHP Creating Secure Websites-XQZT
English | Size: 179.42 MB
Category: Tutorial
Hackers target PHP web applications more often than other sites because most PHP code is written by developers with little security experience.
Software → Cyrobo Secure File Deleter Pro v6.08
Published by: BaDshaH on 23-05-2021, 12:05 |  0
0
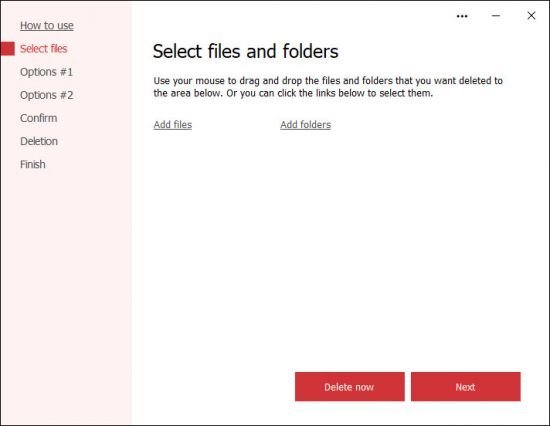
Windows (x64) | File size: 2.5 MB
This tool will permanently wipe the contents of deleted files so that nobody would be able to recover them, even with the use of special tools. The contents of deleted files will be overwritten using random data. You can choose many security algorithms for data destruction.



